The Swedish Cybersecurity Law (CSL), enforcing the NIS2 Directive, came into effect on January 15, 2026. In response, organizations affected by the legislation have taken different approaches. Some focused on closing their CSL compliance projects by that date, while others are preparing to start their work. Some deliberately chose to wait. Others have worked intensively for months to prepare.
Despite these different starting points, they all face the same underlying risk: mistaking completion for capability.
There is a fundamental difference between studying to build real understanding and cramming the course material the night before an exam. One changes how you think and act in the longer term. The other optimizes for passing the test. Many CSL compliance projects, operating under both time and budget pressure, risk resembling the latter. High-intensity, one-off activity, extensive documentation, and visible progress, but with limited impact on how the organization actually operates.
The question is not whether the audit is passed, but what has genuinely improved?
When Methodology Shapes the Outcome
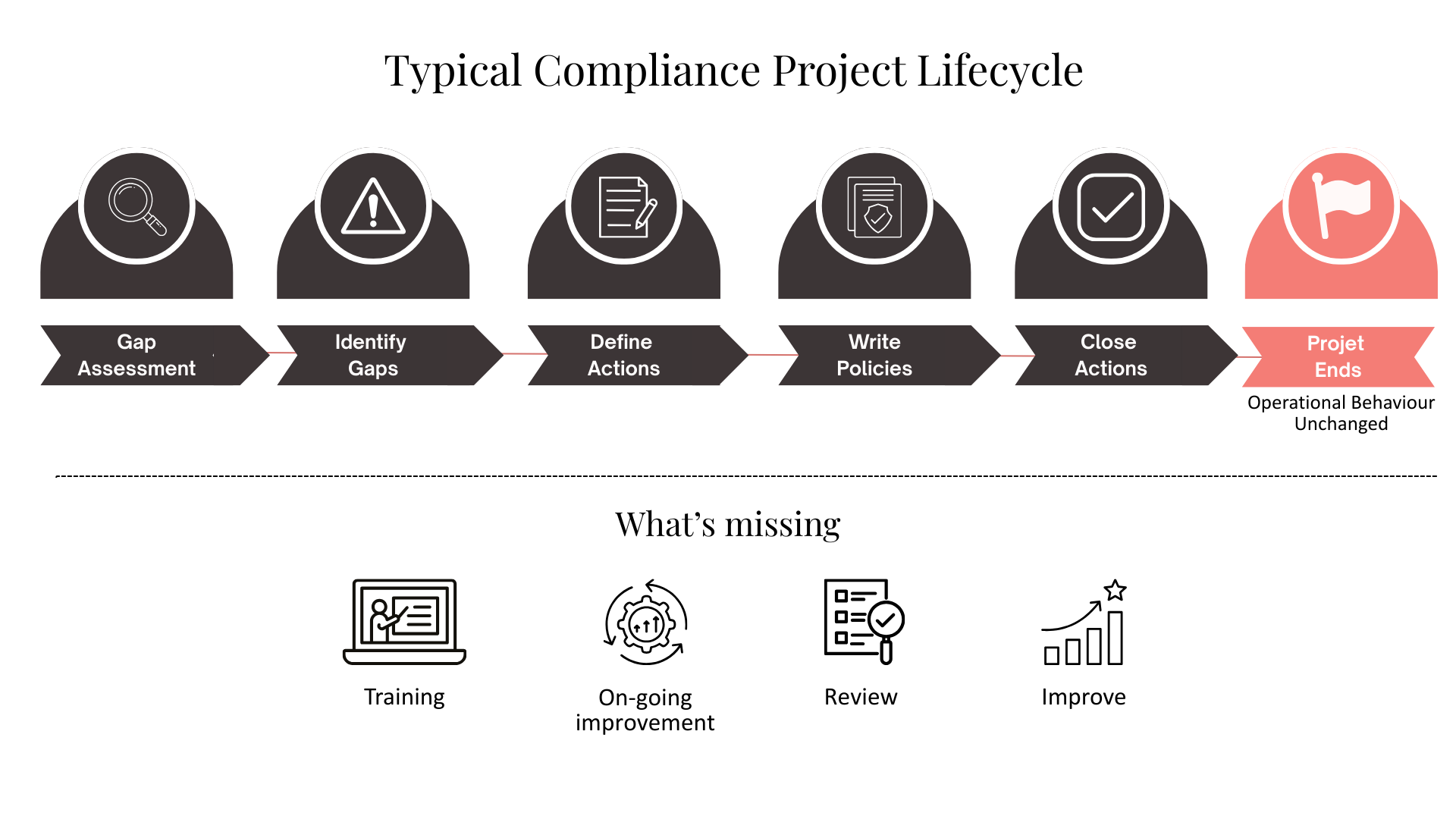
Most compliance projects start with a gap assessment. Existing controls are mapped to the directive, gaps are identified, and remediation initiatives are launched. This approach is legitimate and often necessary. However, it also shapes what the organization optimizes for.
Under time pressure, initiatives to close gaps tend to produce static snapshots of compliance that favor documentation followed by closure. Actions are often defined to “fix” gaps through policies, procedures, or one-time efforts that are easy to approve and close. Findings are frequently treated as binary: compliant or non-compliant. This can often lead to that the operational impact fades over time. Continuity plans and exercises become outdated. Risk assessments turn into periodic activities rather than living inputs to decisions. Processes designed to support resilience are gradually sidelined by other, more prioritized initiatives.
What is rarely examined is whether these measures change day-to-day behavior. A documented process does not mean it is used. As a result, organizations can achieve a high degree of formal compliance while remaining operationally fragile.
Audit Readiness Versus Operational Readiness
Another revealing aspect of compliance projects is how success is measured. In most cases, success equals completion. Actions closed. Deliverables approved. Projects formally ended.
What is rarely measured is improved resilience. Few projects track whether risk-based decisions are being made, whether continuity considerations influence planning, or whether cyber risks are actively discussed outside the security function.
This drives predictable behavior. Organizations invest heavily in steering documents, policies, and frameworks because these are visible and auditable. Far less attention is paid to change management, training beyond initial rollouts, or reinforcement of new ways of working.
When the primary success criteria is completed actions and approved documents, the organization has optimized for auditability rather than operational resilience. Confidence in improved resilience is therefore often assumed rather than evidenced.
The organization is considered safer, but it cannot be clearly explained why.
CSL’s Intent Risks Being Undermined in Practice
This potential outcome is paradoxical because CSL explicitly mandates a risk-based and continuous improvement approach. For organizations familiar with ISO 27000 or quality management disciplines, this way of working is nothing new. For others, it represents a shift away from binary compliance thinking.
Our experience is that many organizations risk undermining the legislation’s original intent. Faced with fixed deadlines, constrained budgets, and pressure to close actions, they default to a project mindset focused on closure rather than on risk management, continuous improvement, and long-term capability.
A risk-based approach requires accepting that not everything can or should be fixed at once. It requires leaders to make informed decisions about where to invest effort and where to consciously accept risk. For organizations used to clear pass or fail criteria, this is often uncomfortable.
Our View: Compliance as a Starting Point, Not an Outcome
Our view is that CSL compliance must be treated as a foundation, not a finish line. Real capability exists only when new processes are followed, when continuous improvement is embedded in normal operations, and when a risk-based mindset is established across the organization.
This requires viewing CSL from a dual perspective. Our proven approach combines assessment of structural elements such as policies, governance, and accountability with a practical examination of how requirements are incorporated into operational processes and handled in real-life situations. We also explicitly consider resource allocation, training, and continuous improvement to ensure that action plans are realistic, risk-based, and sustainable.
The objective is not only to demonstrate compliance, but to strengthen cyber resilience in practice.
Before Declaring Success, Ask This
True operational resilience requires more than updated documentation. It requires risk management, continuity, and cyber resilience to be embedded in everyday planning, decision-making, and leadership behavior.
Compliance provides evidence. Capability determines outcome.
Once the compliance work is completed and the audit has been passed, the essential question for IT and business leaders remains: if a serious incident occurs tomorrow, would the organization act in a better way than it did before the work began?
If the answer is unclear, the organization may have achieved formal compliance, but it has not yet achieved sustained improvement.